Shiba Inu Offers 50 ETH Bounty to Recover Shibarium Stolen Funds

The Shiba Inu team has released a new update on the Shibarium bridge hack and introduced a bounty program to recover stolen assets.
For context, the September 12 exploit drained millions from the Ethereum layer-2 network and left the community facing one of its most serious challenges to date.
Shiba Inu Team Launches 50 ETH Bounty
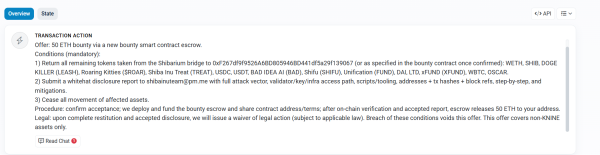
In the latest update, the Shiba Inu ecosystem team revealed that they teamed up with K9 Finance to create a bounty program that offers the attacker 50 ETH ($229,000) if they return the stolen tokens. Notably, the reward sits in a dedicated escrow contract.
The Shib team has joined @K9finance to offer a bounty to the Shib Bridge Exploiter
Shib Deployer 2 has sent a message offering a 50 ETH bounty in exchange for the tokens stolen.https://t.co/7T7AtywqWm pic.twitter.com/Zqq376CnOo
— Shib (@Shibtoken) September 17, 2025
Moreover, the team also set conditions for the bounty. Specifically, the attacker must prepare a whitehat disclosure report that lays out the full method of the exploit.
This includes details on how they gained validator access, the scripts and tools they used, the addresses involved, the transaction hashes, and recommended steps for prevention.
Shiba Inu Team Offers Bounty to Shibarium Hacker
In addition, the attacker must also stop moving the compromised tokens. Once the tokens return and the team verifies the report, the bounty escrow will release 50 ETH to the attacker’s wallet.
Moreover, the developers added that if the attacker complies, they will not pursue legal action and will issue a waiver, provided this falls within the law. However, they clarified that the bounty excludes KNINE tokens, which K9 Finance already secured.
For context, the K9 Finance team has already issued its own bounty of 5 ETH for the KNINE tokens. Notably, the team froze over $700,000 worth of KNINE, which the hacker gained control of. Now that they cannot spend the assets, the team has offered a 5 ETH bounty for their return.
Updated Account of the Shibarium Hack
Meanwhile, alongside the bounty program, the Shiba Inu ecosystem team shared an updated account of how the exploit happened.
Shibarium Bridge Exploit Community Update 17/09/2026
The attacker executed a flash loan swap to acquire 4.6M $BONE from Shibaswap & used those to delegate them to Ryoshi Validator 1. This gave the attacker > 2/3 majority voting on Shibarium validators & the ability to use the…
— Shib (@Shibtoken) September 17, 2025
The team said the attacker executed a flash loan swap to acquire 4.6 million BONE from ShibaSwap. They then delegated the tokens to Ryoshi Validator 1, which gave them more than two-thirds of validator voting power. With this control, they used compromised internal validator keys to sign a malicious state, draining $4.1 million from the bridge.
On-chain records show the attacker stole 17 different tokens. Losses included $1 million in ETH, $1.3 million in SHIB, $717,000 in KNINE, $680,000 in LEASH, and $260,000 in ROAR, along with smaller amounts of other tokens.
The attacker sold only their USDT and USDC by converting them into ETH. They also tried seven times to sell $700,000 worth of KNINE, but K9 Finance blocked the wallet before the sales went through. The attacker still holds the other stolen assets, with the Shiba Inu tokens sitting across more than eight wallets.
Notably, the developers believe a compromise of Shibarium validator keys caused the breach. They suspect the attacker may have gained access either through a developer’s machine or the server’s key management system. In response, they suspended bridge operations and began forensic analysis.
To contain the damage, the team revoked root chain manager access from the proof-of-stake bridge, extended the exit time on the plasma bridge, and disabled predicate burn-only functions to stop further withdrawals. They also flagged suspicious transactions and ruled out the cross-chain contract, which some initially thought caused the breach.
Shiba Inu Team Promises Stronger Security
In the recent disclosure, the Shiba Inu team promised stronger security going forward. They said they will improve monitoring and alerts and tighten internal security practices. They also plan to publish a full post-mortem report once the investigation concludes.
Notably, this update follows earlier analyses from industry figures and security firms. For instance, Tikkala Security and Pulse Digital claimed there were deeper governance issues, mentioning how the hack also involved leaked keys and manipulated Merkle roots.
 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  USDC
USDC  Wrapped SOL
Wrapped SOL  JUSD
JUSD  TRON
TRON  Lido Staked Ether
Lido Staked Ether  Dogecoin
Dogecoin  Figure Heloc
Figure Heloc  WhiteBIT Coin
WhiteBIT Coin  Cardano
Cardano  Bitcoin Cash
Bitcoin Cash  Wrapped stETH
Wrapped stETH  Wrapped Bitcoin
Wrapped Bitcoin  USDS
USDS  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  LEO Token
LEO Token  Monero
Monero  Wrapped eETH
Wrapped eETH  Hyperliquid
Hyperliquid  Chainlink
Chainlink  Canton
Canton  Ethena USDe
Ethena USDe  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Stellar
Stellar  WETH
WETH  USD1
USD1  Zcash
Zcash  Litecoin
Litecoin  USDT0
USDT0  Dai
Dai  sUSDS
sUSDS  Avalanche
Avalanche  Sui
Sui  Shiba Inu
Shiba Inu  Hedera
Hedera  Ethena Staked USDe
Ethena Staked USDe  PayPal USD
PayPal USD  World Liberty Financial
World Liberty Financial  Tether Gold
Tether Gold  Rain
Rain  Toncoin
Toncoin  Cronos
Cronos  Polkadot
Polkadot  Uniswap
Uniswap  MemeCore
MemeCore  Mantle
Mantle  Falcon USD
Falcon USD  Bitget Token
Bitget Token  PAX Gold
PAX Gold  Aave
Aave  OKB
OKB  Bittensor
Bittensor  Pepe
Pepe  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Circle USYC
Circle USYC  HTX DAO
HTX DAO  Global Dollar
Global Dollar  Jupiter Perpetuals Liquidity Provider Token
Jupiter Perpetuals Liquidity Provider Token  NEAR Protocol
NEAR Protocol  syrupUSDC
syrupUSDC  Pump.fun
Pump.fun  Ethereum Classic
Ethereum Classic  Internet Computer
Internet Computer  Jito Staked SOL
Jito Staked SOL  Sky
Sky  Binance-Peg WETH
Binance-Peg WETH  Ripple USD
Ripple USD  Pi Network
Pi Network  Ondo
Ondo  BFUSD
BFUSD  Aster
Aster  Binance Bridged USDC (BNB Smart Chain)
Binance Bridged USDC (BNB Smart Chain)  Wrapped BNB
Wrapped BNB  KuCoin
KuCoin  Gate
Gate  Worldcoin
Worldcoin  Binance Staked SOL
Binance Staked SOL  POL (ex-MATIC)
POL (ex-MATIC)  Ethena
Ethena  USDD
USDD  MYX Finance
MYX Finance  Aptos
Aptos  Rocket Pool ETH
Rocket Pool ETH  Cosmos Hub
Cosmos Hub  Official Trump
Official Trump  Algorand
Algorand  Lombard Staked BTC
Lombard Staked BTC  Polygon Bridged USDC (Polygon PoS)
Polygon Bridged USDC (Polygon PoS)  USDtb
USDtb  Superstate Short Duration U.S. Government Securities Fund (USTB)
Superstate Short Duration U.S. Government Securities Fund (USTB)  Function FBTC
Function FBTC  syrupUSDT
syrupUSDT  NEXO
NEXO  Arbitrum
Arbitrum  Midnight
Midnight  Render
Render  Filecoin
Filecoin  WrappedM by M0
WrappedM by M0  Janus Henderson Anemoy AAA CLO Fund
Janus Henderson Anemoy AAA CLO Fund  Ondo US Dollar Yield
Ondo US Dollar Yield  VeChain
VeChain  OUSG
OUSG  Kinetiq Staked HYPE
Kinetiq Staked HYPE  Mantle Staked Ether
Mantle Staked Ether  Spiko EU T-Bills Money Market Fund
Spiko EU T-Bills Money Market Fund  Polygon PoS Bridged DAI (Polygon POS)
Polygon PoS Bridged DAI (Polygon POS)  Solv Protocol BTC
Solv Protocol BTC  USDai
USDai  Bonk
Bonk  COCA
COCA  Liquid Staked ETH
Liquid Staked ETH  Beldex
Beldex  Arbitrum Bridged WBTC (Arbitrum One)
Arbitrum Bridged WBTC (Arbitrum One)  clBTC
clBTC  Wrapped Flare
Wrapped Flare  Usual USD
Usual USD  Janus Henderson Anemoy Treasury Fund
Janus Henderson Anemoy Treasury Fund  Jupiter
Jupiter  Sei
Sei  Dash
Dash  L2 Standard Bridged WETH (Base)
L2 Standard Bridged WETH (Base)  StakeWise Staked ETH
StakeWise Staked ETH  Binance-Peg XRP
Binance-Peg XRP  Renzo Restaked ETH
Renzo Restaked ETH  Story
Story  A7A5
A7A5  GHO
GHO  PancakeSwap
PancakeSwap  TrueUSD
TrueUSD  Tezos
Tezos  Jupiter Staked SOL
Jupiter Staked SOL  Chiliz
Chiliz  Pudgy Penguins
Pudgy Penguins  Arbitrum Bridged WETH (Arbitrum One)
Arbitrum Bridged WETH (Arbitrum One)  tBTC
tBTC  Stable
Stable  Stacks
Stacks  Optimism
Optimism  Lorenzo Wrapped Bitcoin
Lorenzo Wrapped Bitcoin  c8ntinuum
c8ntinuum  EURC
EURC  Artificial Superintelligence Alliance
Artificial Superintelligence Alliance  Curve DAO
Curve DAO  Resolv USR
Resolv USR  Virtuals Protocol
Virtuals Protocol  Resolv wstUSR
Resolv wstUSR  GTETH
GTETH  Steakhouse USDC Morpho Vault
Steakhouse USDC Morpho Vault  DoubleZero
DoubleZero  Lighter
Lighter  JUST
JUST  Ether.Fi Liquid ETH
Ether.Fi Liquid ETH  Kinesis Gold
Kinesis Gold  Injective
Injective  sBTC
sBTC  BitTorrent
BitTorrent  LayerZero
LayerZero  Lido DAO
Lido DAO  Marinade Staked SOL
Marinade Staked SOL  Aerodrome Finance
Aerodrome Finance  Ether.fi
Ether.fi  Maple Finance
Maple Finance  AINFT
AINFT  Sun Token
Sun Token  ether.fi Staked ETH
ether.fi Staked ETH  Decred
Decred  FLOKI
FLOKI  Coinbase Wrapped Staked ETH
Coinbase Wrapped Staked ETH  Kaia
Kaia  The Graph
The Graph  Kinesis Silver
Kinesis Silver  crvUSD
crvUSD  Celestia
Celestia  Stader ETHx
Stader ETHx  Staked Aave
Staked Aave  Bitcoin SV
Bitcoin SV  IOTA
IOTA  Cap USD
Cap USD  Axie Infinity
Axie Infinity  Gnosis
Gnosis  Pyth Network
Pyth Network  Binance-Peg BUSD
Binance-Peg BUSD  Starknet
Starknet  Avalanche Bridged BTC (Avalanche)
Avalanche Bridged BTC (Avalanche)  Wrapped ApeCoin
Wrapped ApeCoin 